Automotive Cybersecurity and Physical Security
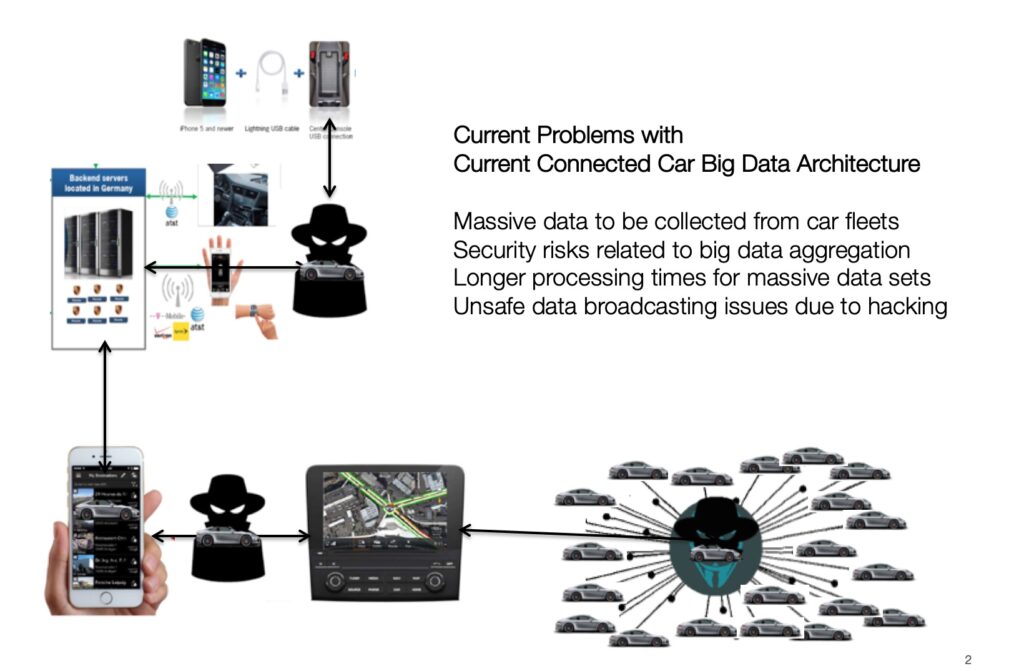
In an era where connected cars are becoming increasingly prevalent, the need for robust cybersecurity measures is more critical than ever. There is an evident need for protection from many different RF wireless hacks that have been successful in hacking user credentials and actually stealing all types of connected cars.
Among various innovative solutions, our “LightKey” broadcasting security technology emerges as a cornerstone in the realm of vehicular cybersecurity. This blog article reviews some aspects of our LightKey for automotive technology, in terms of the LightKey value proposition and its pivotal role in safeguarding connected cars against cyber security attacks and against and physical car theft threats.
The Rise of Connected Cars and Associated Cyber Risks
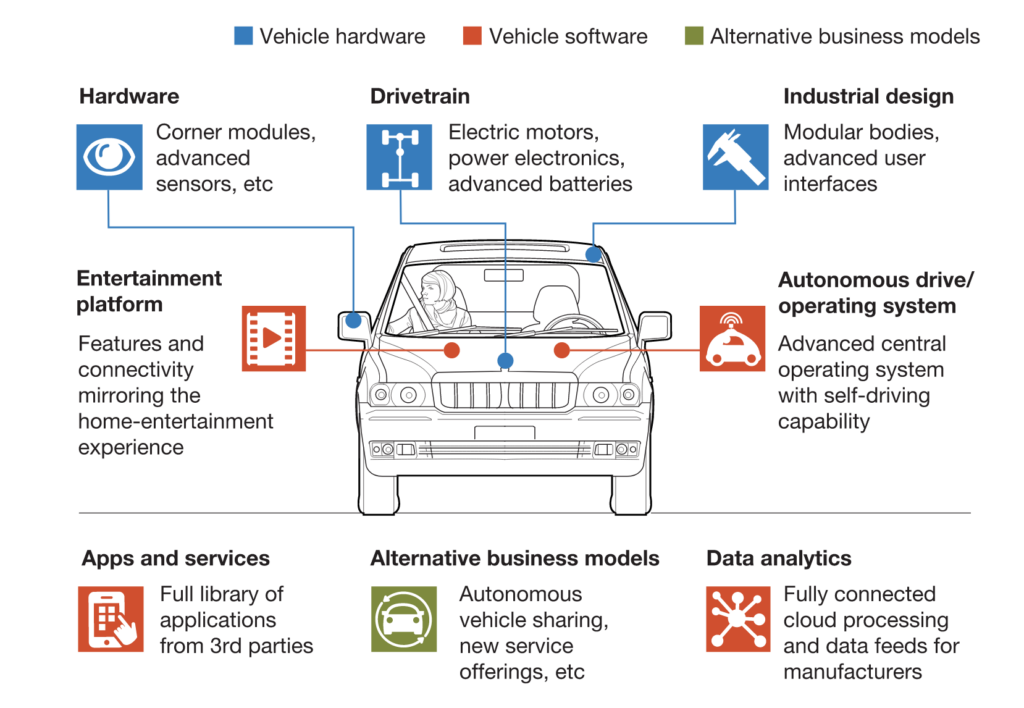
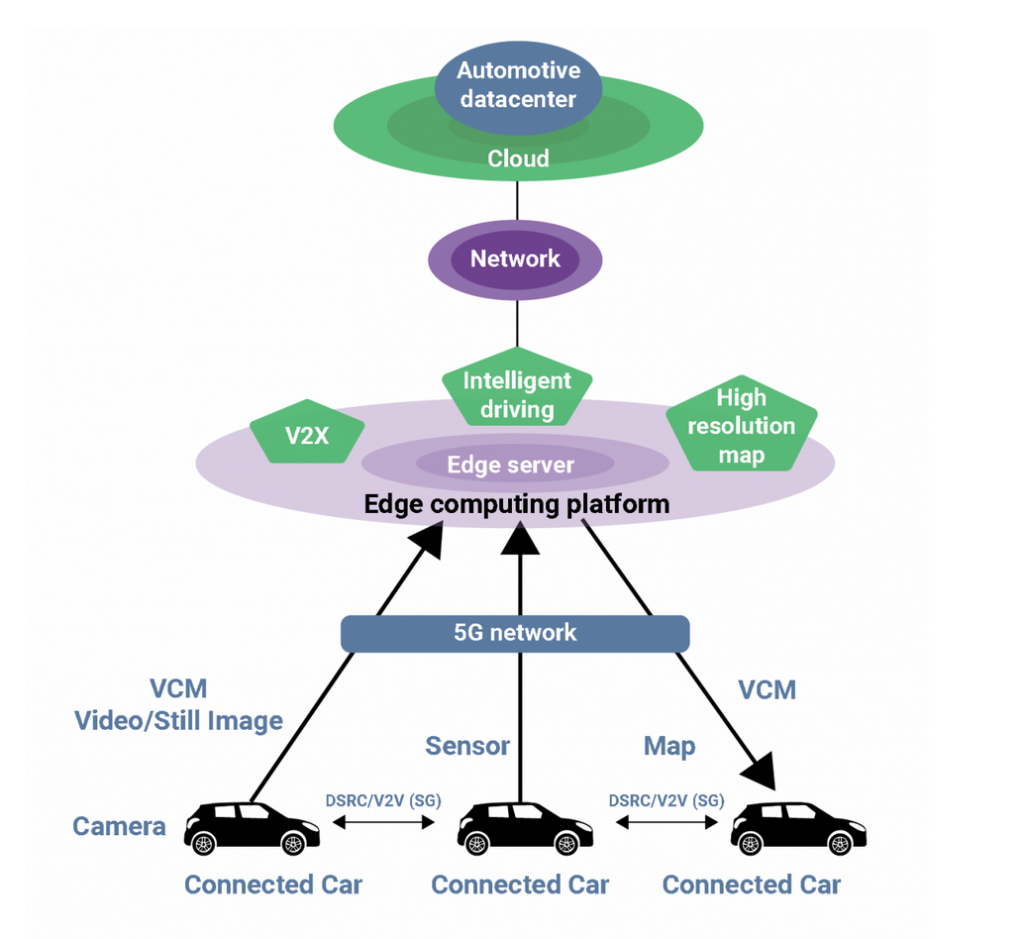
The automotive industry has witnessed a significant shift towards connected vehicles, integrating advanced AI and networked micro-controllers. While these technological advancements offer enhanced functionality and user experience, they also introduce substantial cybersecurity risks. The Controller Area Network (CAN) of these vehicles, crucial for internal communication, typically lacks encryption, making it vulnerable to cyber-attacks. The dire need for secure and authenticated wireless communication systems in connected cars has never been more apparent.
Understanding Light Broadcasting Security Technology
LightKey broadcasting security technology utilizes light signals to authenticate the user of a connected car. This method involves transmitting a unique sequence of light signals that the vehicle owner or authorized user must recognize and respond to correctly. This interaction is facilitated through our mobile LightKey app and/or through our remote user authentication procedures. The uniqueness of the light sequence produced by our LightKey App and devices, make it a robust authentication tool that is hard to replicate or interfere with by unauthorized entities.
Advantages of Light Broadcasting in Vehicle Security
Enhanced Authentication: The light broadcasting system provides a secure and reliable method for authenticating legitimate users, thereby preventing unauthorized access to the vehicle.
Backward Compatibility: This technology can be seamlessly integrated into older vehicle models, making it an ideal solution for retrofitting cybersecurity measures in a vast range of cars.
Low Risk of Interference: Unlike radio frequency-based systems, light signals are less prone to interception or jamming, offering a more secure communication channel.
User-Friendly Interface: With intuitive interaction mechanisms, light broadcasting systems can be designed for ease of use, ensuring that legitimate users are not inconvenienced.
Integrating Light Broadcasting with CAN Systems
To fully harness the potential of light broadcasting technology, LightKey is integrated with the vehicle’s CAN system in a fail-safe and tamper-proof manner. In the event of unauthorized access attempts, the system can issue commands to immobilize the vehicle. This integration not only adds an extra layer of security but also ensures immediate action in case of a breach, safeguarding both the vehicle and its occupants.
Addressing Challenges in Implementation
Implementing light broadcasting security technology involves overcoming several challenges:
Compatibility Across Different Models: The system must be adaptable to various vehicle architectures, ensuring broad applicability.
Ensuring Reliability: The technology must consistently perform under different environmental conditions, maintaining its effectiveness regardless of lighting or weather conditions.
Balancing Security and Convenience: While maximizing security, the system should not overly complicate the user experience or cause undue inconvenience.
The Role of Light Broadcasting in Legal and Insurance Frameworks
Considering legal frameworks like the UK’s 2018 Automated and Electrical Vehicle Bill, which emphasizes the importance of cybersecurity in connected cars, light broadcasting technology can play a significant role. By providing a secure method of user authentication and firmware updates, it aligns with potential legal requirements, thereby mitigating insurance risks associated with cyber vulnerabilities.
Future Prospects and Industry Impact
The adoption of light broadcasting security technology in connected cars could have far-reaching implications for the automotive industry. It sets a precedent for innovative cybersecurity solutions and may inspire the development of standardized security protocols across various manufacturers.
Light broadcasting security technology stands as a pioneering solution in the quest to bolster cybersecurity in connected cars. Its ability to provide secure user authentication, coupled with its integration with the vehicle’s CAN system, marks a significant stride in protecting vehicles from cyber threats. As the automotive industry continues to evolve, embracing such innovative technologies will be crucial in ensuring the security and safety of connected vehicles. Light broadcasting security technology not only addresses current cybersecurity challenges but also paves the way for a safer and more secure automotive future.