The computer and telecommunications industries are today in a dynamic state of convergence with the auto and cybersecurity industries. Such convergence is creating a unique large-scale opportunity for development of a new generation of vehicle computation retro-fit devices that are capable of delivering powerful tamper-proof cybersecurity solutions. Something which is sorely needed and, in order to empower users with an unexpected and truly revolutionary new level of processing power and vehicle security at the edge. In particular, we believe that these industries are yet to create and implement more reliable and more secure wireless technologies. A new approach to existing connected and autonomous vehicle security problems is painfully required, worldwide. A solution that is capable of accelerating the advent of a new generation of “secure connected vehicles.”
We believe there is a clear market opportunity for delivery of much more powerful edge-computing retro-fit hardware into existing and new vehicles. We believe that we must visualize the future by looking through the lens of innovation.
At Quantum Light Ltd, we can see a very clear strategic need to quickly and inexpensively deliver into these markets our new generation of hardware and software retro-fit technologies, secured by our own optical innovation! Millions of insecure connected cars are on the road today, which urgently require a new cybersecurity and edge-computing solution. A new tamper-proof vehicular security solution that may soon help accelerate large-scale deployment of end-to-end, secure and most importantly, regulatory compliant, wireless networks of connected and autonomous vehicles. In the U.K. we have a wide-spread and unsolved connected-vehicle problem. A key and painful problem, which shockingly impacts the owners of most if not all “smart connected vehicles.” There are literally millions of connected and autonomous vehicles, which are currently suffering from poor hardware security.
A serious problem, significantly impacting connected car markets and limiting their potential. Consider the fact there are over 10 million connected vehicles on British roads, which are unable to comply with the 2018 Automated and Electric Vehicle Law, for many reasons! We believe there is clear and very large market demand for securing connected vehicles. We have in our hands an opportunity to help solve a mission-critical obstacle in the path to deployment of automated and connected vehicles.
Edge computing for cars is powerful but not enough. Secure communications require more edge-computation power. Connected and AI self-driving cars require much higher mission-critical levels of communications’ cybersecurity. Connected and self-driving vehicles are vulnerable and we have to address these flaws as soon as possible.

The “Internet-of-things” along with the advent of car electronic control units or microprocessors for “wireless connected cars” may perhaps be compared to a similar “convergence point” in the computer industry during the 1970 to 1979 period. I can see an applicable system topology metaphor: personal computers versus the Mainframe terminals? The answer was of course that users demand more computation power in their hands. I think we can extrapolate the same paradigm and realise that there is a need for more computation power in the car, at the edge. We need more local power.
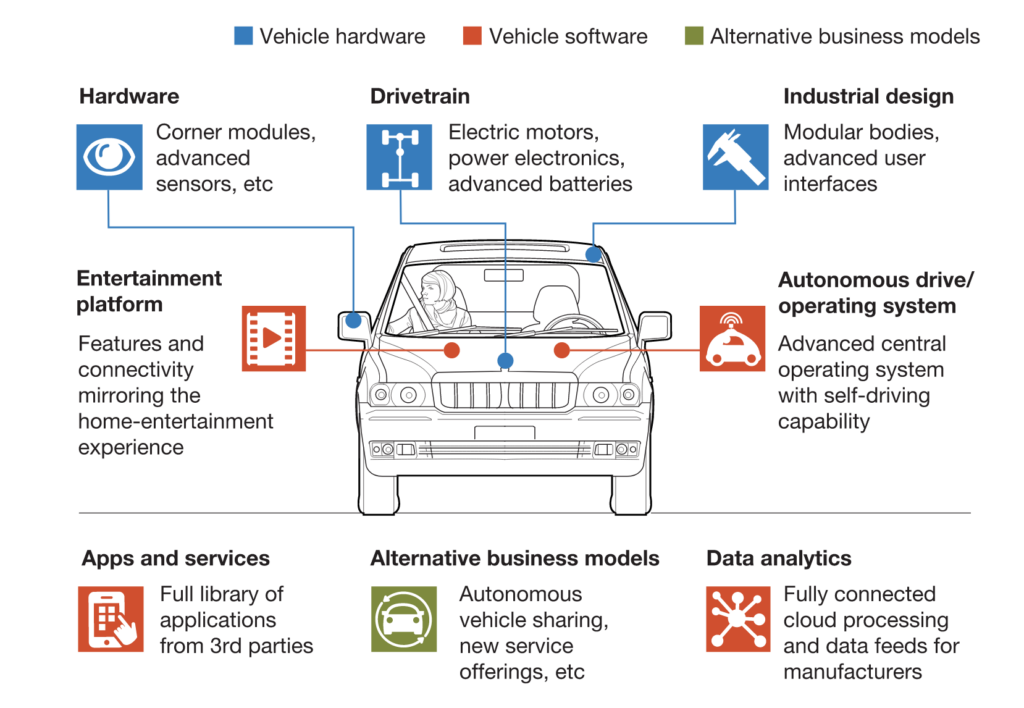
In terms of Cybersecurity, it’s necessary to speed up development of the connected car’s Cybersecurity architecture. At the moment, most cars rely on typical centralized Server network topologies, exposing unencrypted internet traffic to and from cars.
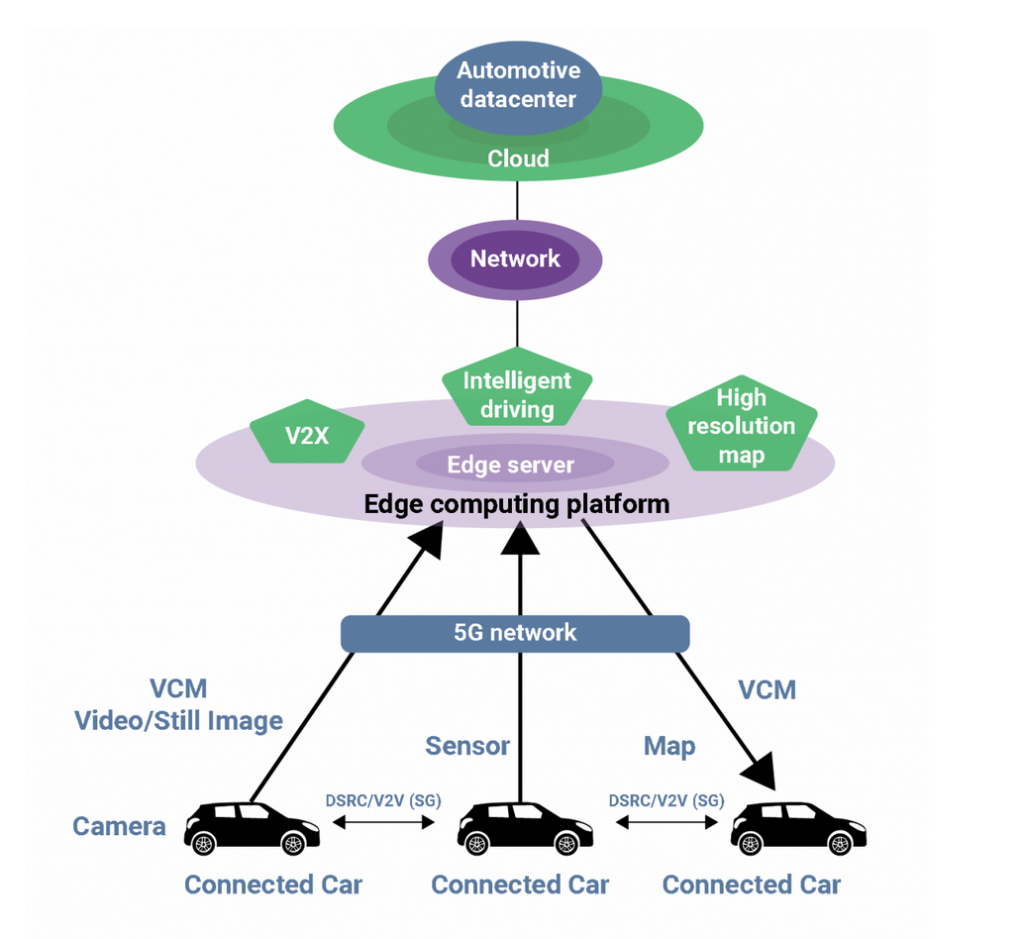
We are faced with Cybersecurity problems in connected cars, despite the obvious powerful computer smarts of modern connected AI self-driving cars and even considering the remarkable computation power derived from over 100 individually networked micro-controllers or mini-computers on-a-chip, all part of the car’s brains. We may also find in “connected AI self-driving” automobiles, an estimated 100 million lines of car computer code are running at once.
Alas! despite of all these marvelous microcontrollers, not much power “at the AI car edge” is dedicated to wireless communications. Cybersecurity cannot be achieved at the edge by software alone, since the entire “Controller Area Network” of each car is unprotected. There is no encryption of data flowing in the CAN network of cars, which is the internal hardware network that connects all components in modern cars.
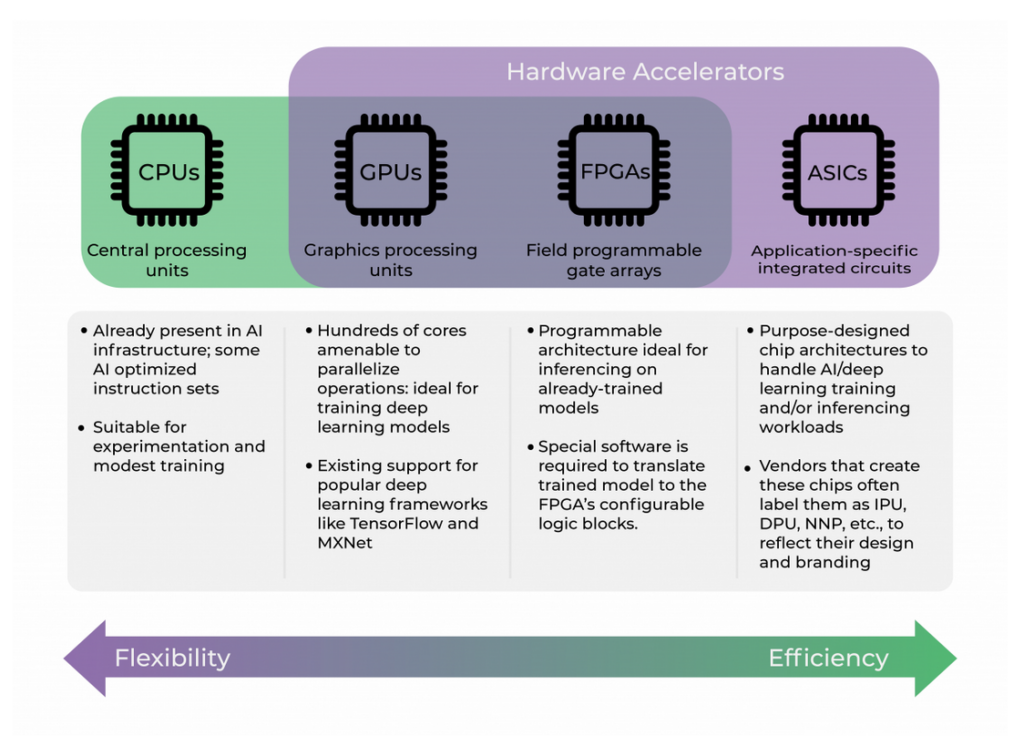
The UK 2018 Automated and Electrical Vehicle Bill may one day require owners to install a specialized connected car Cybersecurity device, or else incur serious Insurance risk in cases of accidents for cars that operate with any level of self-driving AI software. An insurance liabiilty risk exists in the UK when, after an accident it is determined there were no secure firmware updates for the car’s operating AI software. It is hard to believe, but currently most if not all connected cars… cannot comply with this UK Law and physically due to the nature of their on-board electronics, cannot update AI firmware using secure and authenticated wireless transmissions.

https://www.legislation.gov.uk/ukpga/2018/18/section/4/enacted
Therefore, despite the technological marvels offered by connected cars today (like driving a collection of small computers on wheels) we are still not safe in terms of Cybersecurity since each one element of this automotive “Controller Area Network” does not have encryption and no way to update AI firmware wirelessly under secure authentication. There are no software “patches” possible to a hardware problem.
The automotive industry has NO shared security standards for different automotive vendors of electronic parts. Since each new part has no built-in credible Cybersecurity… once connected to the Internet, cars could become a hacking target. (2)
Hacking attacks on a “Connected Car” pose a significant risk due to the fact the car’s “Controller Area Network” manages in-car messages from different mission critical car systems, which many times may be life-critical to the driver and to the safety of other cars in proximity to the vehicle. The most vulnerable “attack vectors” are of course the user credentials & smartphone devices, which are also prone to hacking security keys and it’s best not to mention other attack vectors that pose significant “fleet” risk.
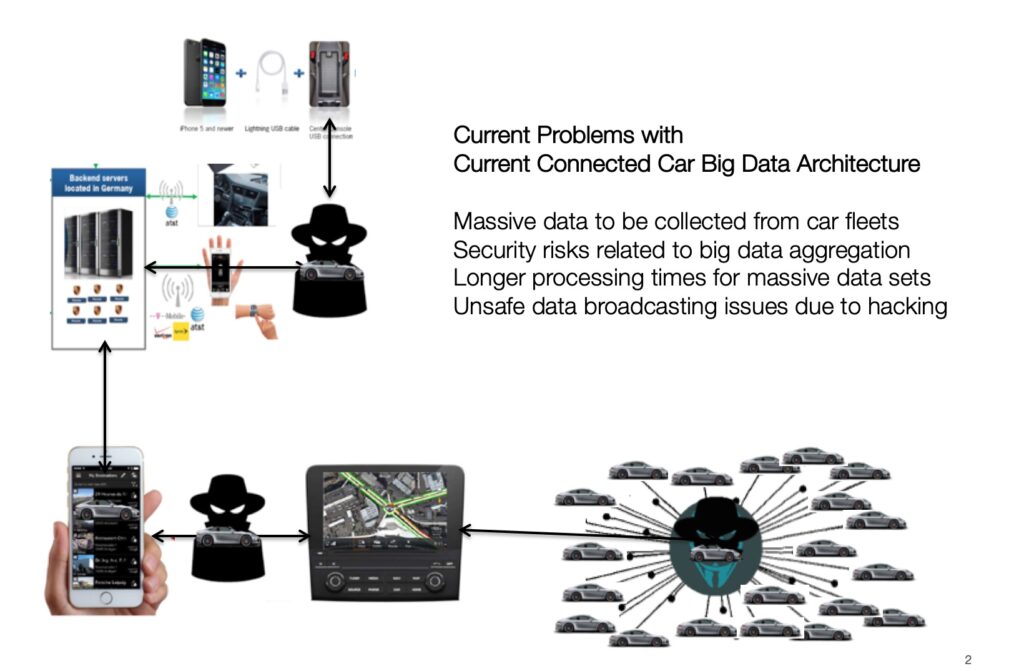
As the car industry moves faster to develop better self-driving artificial intelligence vehicles, it becomes ever more critical to invent new solutions that offer robust network security from hacking intruders. This problem presents a significant risk for users and also for car manufacturers, as well as for the Insurance industry, since the costs of insurance coverage reflect implicit security risks in today’s digital economy.
In the future, we venture to forecast that it will not be possible to legally operate self-driving cars on UK motorways without a hardened on-board computational and secure wireless communications system for certification of the roadworthiness and reliability of such autonomous vehicles. Encrypted, secure and authenticated wireless frequent updates of critical self-driving firmware software, requires the installation of a retrofit tamper proof, new genertion “firewall” security communications device: AEBIS.
Our need for incorporating an entire new level of effective Cybersecurity to vehicle manufacturing is becoming increasingly demanding; in order to resolve the issues of safety and system integrity for more than 10 million connected cars on UK motorways alone. We respectfully and humbly posit, Connected Car Cybersecurity is a strategic imperative for the future of AI autonomous and connected vehicles to the Internet.
Floren Cabrera F. de Teresa, CEO
https://www.pcmag.com/news/the-forgotten-world-of-dumb-terminals
I

